Disposable Virtual Machines: Deliberately Expendable
“Processor virtualization” is trendy. It is a buzzword often used in corporate and professional IT. While undoubtedly highly useful in professional contexts; processor virtualization has far wider applicability. Disposable Virtual Machines are one such use.
Security is not solely the province of corporate computers. Home computers share many of the same security concerns. User accounts can be completely locked-down; but the lockdown precludes a variety of activities. Also, few households have dedicated system management teams.[1] About two years ago, I encountered an externally imposed requirement that well-illustrates this dilemma.
Webinars have been embraced wholeheartedly by organizations large and small. Meetings and courses formerly presented in-person are now offered remotely via the Internet. The trend toward webinars is driven by straightforward economics. Webinars are generally cheaper per capita than live seminars. There is no need for a conference facility. Travel is no longer necessary for students and instructors. The cost savings are substantial.
However, two-way communication is necessary to allow student-presenter interaction. Typically, this requires the installation of software to enable interaction on the attendee's system. Therein lies a challenge:
- software installations require management-level rights
- many organizations require pre-approval for plug-ins, Active-X and similar technologies
The requirement to install software makes participation in the webinar problematic. Participation requires the installation of non-standard software. Security policies that protect the computer integrity from the hazards of unauthorized and unvetted software make the installation of special-purpose software problematical. Limitations on the attendee's choice of platform and web browser only serve to exacerbate this problem.
Often, webinar sponsors only permit limited choice in attendee environments. It is common to limit the choice to a single web browser per platform. While you may want to participate in the webinar from your iPod Touch, the iPod Touch may not be a supported platform. Even if Safari (the standard supplied web browser on iPod Touch) is supported on the iPod Touch; Safari may not be a supported web browser on other platforms. In effect, the sponsor of the webinar forces attendees to adopt the platforms and supporting software chosen; there is no choice or accommodation for differing policies and requirements. The question of platform choice is a topic for another installment.
This particular webinar sponsor, who shall remain nameless, required that participants use either:
- Microsoft Windows – Internet Explorer; or
- Linux – Firefox
While there was a Java-implementation for the Linux-Firefox context; that very same Java-implementation was not supported in the Microsoft Windows milieu. In the Windows environment, the prerequisite for webinar participation was the use of Internet Explorer with the additional installation of a sponsor-supplied, downloadable ActiveX-control. For a number of security-related reasons, It is my policy to minimize the use of Active-X controls on my systems.[2] My request to use the Java/Firefox implementation on Windows was met by “You must use Internet Explorer on Windows”. When I mentioned security concerns, the response was reminiscent of a teenage classic: “Trust us”. It goes without saying that these responses did little to allay my concerns. I have no desire to remediate an avoidable security incident.
Considering the intransigence of the situation, I realized it would be necessary to satisfy two apparently contradictory requirements: preserving the integrity of my workstation while installing an Active-X control in Internet Explorer. My answer was to use a virtual machine, particularly a virtual machine whose use was limited to this particular instance, hence a “disposable virtual machine”. The use of a disposable virtual machine to host the required Active-X control eliminated the conflict between my two goals.
Since the webinar all but required the use of Windows, I decided to use Microsoft's Virtual PC 2007 software to create a virtual Windows system. I could then install the mandated Active-X control within the virtual Windows XP system. This solution would satisfy the imposed requirement of using Internet Explorer on Windows with a custom Active-X control for the webinar; without compromising the security of my workstation.
I quickly created a virtual machine, installed Windows XP on it, downloaded and installed the Active-X control, and participated in the webinar. When the webinar was finished, I shut down the virtual machine until the next webinar. My workstation remained pristine and secure.
Several weeks after that episode, I encountered a somewhat similar problem in a different vein: warring VPN implementations. In my consulting practice, I deal with many different clients. While I do much of my research on in-house systems, there is often a need to connect to client systems. In days past, dial-up modems were the common method for establishing communications with remote systems. Today, dial-up modems are all but extinct; most clients prefer to use an encrypted Virtual Private Network (VPN) to provide a secure communications channel to their internal systems. The public Internet is used as a transport facility for the encrypted channel.
However, there are a wide variety of VPN implementations; each with a different client-side software component. This is not a problem for employees, who use a single VPN to access their place of employment. In my case, it is a significant problem. Each client requires that I install the VPN package they have chosen to secure communications with their network. In some cases, clients are using different (and incompatible) versions of the same VPN package.
This diversity of VPN software had already caused a series of problems in my consulting practice. I had already experienced a series of problems whose root cause was either:
- different clients using different versions of the same VPN software; or
- different VPN packages being incompatible with each other
In some cases, the result was a non-functioning VPN package; in a few cases the result was the infamous BSOD.[3] Using a Disposable Virtual Machine allowed me to isolate each of the disparate VPN packages from each other.
Implementing this approach required several steps. The first step was to create a base Microsoft Windows XP Service Pack 3 system, with all subsequent updates. Then, I installed several common packages (e.g., Firefox, Kermit).
Once I created this basic environment, I froze the “disk”, and marked it as Read- only. I then used a feature of Microsoft's Virtual PC 2007 software referred to as a “differencing disk”.[4] Rather than directly use the virtual base Windows XP system disk as the virtual machine's disk image, I created a separate differencing disk for each client using the now read-only base Windows XP system disk as a foundation. I then used the differencing disk as the system disk for each client virtual machine. I then installed the VPN software used by an individual client on that unique disk image.
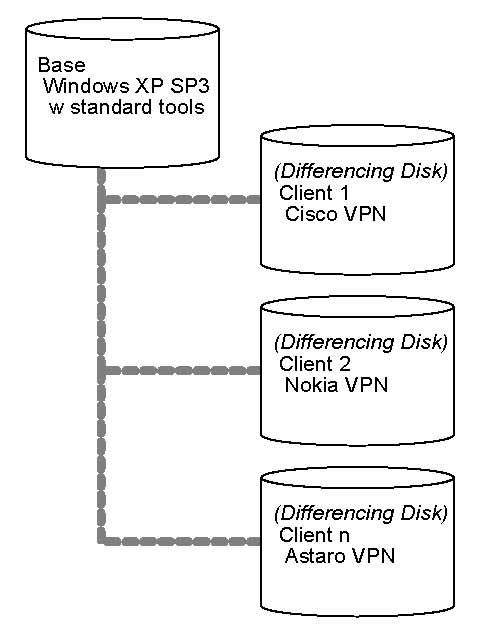
|
| Base Windows XP SP3 System Disk with Different VPN packages on client-specific differencing disks |
The Disposable Virtual Machines approach is not a panacea. However, disposable vitual machines do have significant advantages for those who need to transiently host a variety of software for temporary or intermittent use.
This approach was presented at the 2010 Trenton Computer Festival under the title Disposable Virtual Machines. The slides from that presentation are available at http://www.rlgsc.com/trentoncomputerfestival/2010/disposable-virtual-machines.html.
Disposable Virtual Machines are an example of how an innovative re-examination of problems from a different perspective can resolve seemingly irresolvably conflicts in requirements.
Notes
| [1] | Several years ago, I spoke at an IEEE Communications Society seminar with several other senior technologists. One of my fellow presenters, an executive with IBM, related how she and her husband were converting their home network to what is now referred to as “thin- client”, with the goal of eliminating overtime for the in-house system management team (the need for her and her husband to spend Christmas vacations on system administration tasks for their family's entourage of personal computers). |
| [2] | R Gezelter (2003) “Mobile Code” Chapter 10 in Computer Security Handbook, 4th Edition John Wiley & Son, |
| [3] | BSOD - Blue Screen of Death (A Windows Kernel Exception) |
| [4] | A differencing disk stores the disk blocks that differ from the original disk. In the example cited of a Windows XP disk with several layered products, the differencing disk is a fraction the size of the underlying disk. |
References
- S. Bosworth and M. Kabay (2002) Computer Security Handbook, 4th Edition John Wiley & Sons, New York.
- R. Gezelter (2002) “Mobile Code” Chapter 10 in Computer Security Handbook, 4th Edition. Chapter outline available at http://www.computersecurityhandbook.com/csh4/chapter10.html
- R. Gezelter (2010, April 24) “Disposable Virtual Machines” Presentation at the Trenton Computer Festival. Sponsored by ACM, IEEE Computer Society. Slides retrieved from http://www.rlgsc.com/trentoncomputerfestival/2010/disposable-virtual-machines.html on August 16, 2010











![Validate my Atom 1.0 feed [Valid Atom 1.0]](http://images.rlgsc.com/logos/valid-atom.png)
![Validate my RSS feed [Valid RSS]](http://images.rlgsc.com/logos/valid-rss.png)